Sysmon Integration with Qradar
Sysmon-Windows Sysinternal
Irrespective of the built-in logging capabilities of a Windows server, we can configure additional software for substantial host-level auditing.
Sysinternal of Microsoft offers System Monitor (Sysmon) as an add-on for advanced threat auditing by performing system-level deep monitoring, observing traffic activity, tracking code behavior, etc.
It does not generate an alarm or provide analysis or hides its presence from the attackers: instead, it runs as a service in the background and uses system drivers. The article shows how to install Sysmon in Windows and demonstrates how to send its events to Qradar.
Getting Started
Before installation, download a filter file sysmonconfig-export.xml to modify from the Github SwiftOnSecurity page. Before anything, replace the hashes in the following line with an asterisk ‘*’ as one of the best features of Sysmon is that it records hashes of all the system files.
<HashAlgorithms>md5,sha256,IMPHASH</HashAlgorithms><HashAlgorithms>*</HashAlgorithms>
The event filtering as above allows us to filter out noisy events, such that each event has a filter tag. The include for onmatch attribute only includes matched events. We will replace it with the exclude value for event IDs of 7, 9, 10, 17, and 18 to include events other than rule match events. Save the file in a separate folder.
Download Sysmon from the official website, and extract the executables from the .zip files. Use the application as per your architecture: use sysmon64.exe for a 64-bit system. Lastly, transfer the required application to the above folder.
Sysmon Installation
Run the Command-prompt with administrative privileges and cd into the path of the above folder. Execute the following command for Sysmon installation:
Sysmon64.exe -i <configuration_file/sysmonconfig-export.xml>The command prompts to accept the license, and it is complete.
Log Source Creation
Go to the Event Viewer-> Create Custom Views, go to Event Logs in the Filter tab->Applications and Services Logs->Microsoft-> Windows->Sysmon, and select Operational.

Open the XML table to copy the query manually and paste it inside Wincollect XPath.

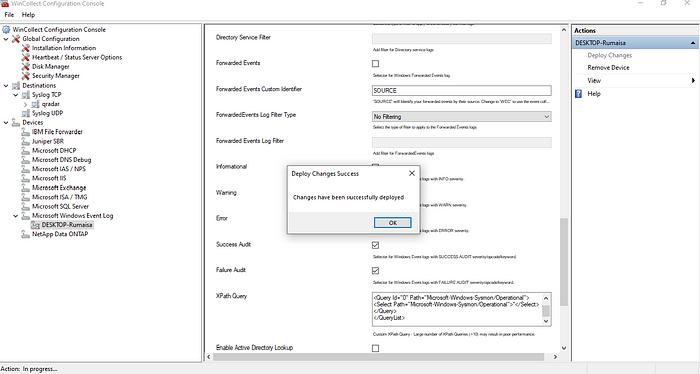
The QRadar contains a Sysmon content extension “IBM QRadar Content Extension for Sysmon” to receive its events (more on this later). Go to the Log Activity and filter out the latest events to verify successful Sysmon Integration with Qradar by checking the packet details.
Happy Learning! (:
